一:介绍
1
2
| 本意是做接口的加解密,找了到了拦截@RequestBody的方法
这里做一下记录。
|
二:方法
2.1 新增注解
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
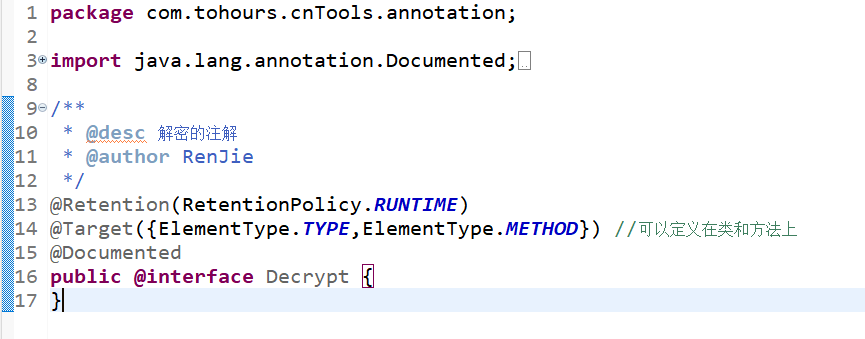
| package com.tohours.cnTools.annotation;
import java.lang.annotation.Documented;
import java.lang.annotation.ElementType;
import java.lang.annotation.Retention;
import java.lang.annotation.RetentionPolicy;
import java.lang.annotation.Target;
/**
* @desc 解密的注解
* @author RenJie
*/
@Retention(RetentionPolicy.RUNTIME)
@Target({ElementType.TYPE,ElementType.METHOD}) //可以定义在类和方法上
@Documented
public @interface Decrypt {
}
|
2.2 DecryptRequestAdvice继承RequestBodyAdviceAdapter
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
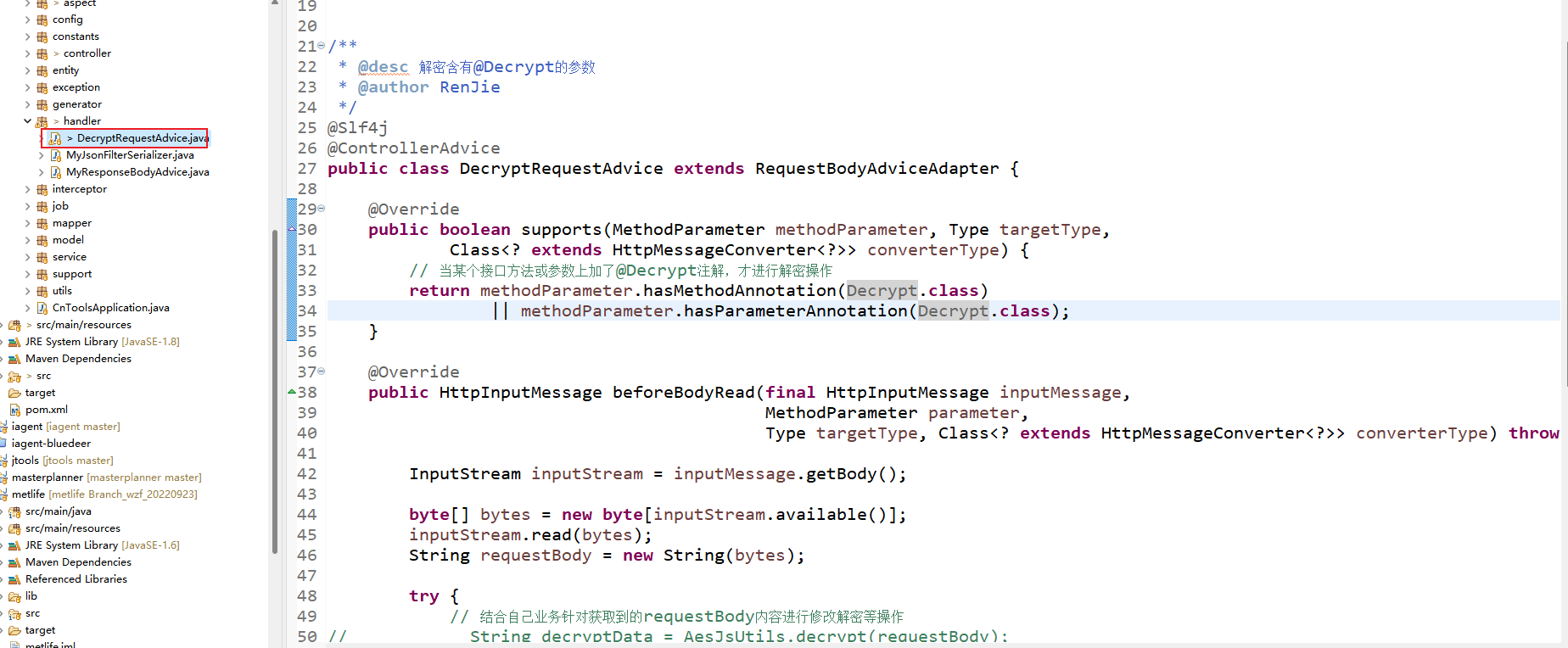
| package com.tohours.cnTools.handler;
import java.io.ByteArrayInputStream;
import java.io.IOException;
import java.io.InputStream;
import java.lang.reflect.Type;
import org.springframework.core.MethodParameter;
import org.springframework.http.HttpHeaders;
import org.springframework.http.HttpInputMessage;
import org.springframework.http.converter.HttpMessageConverter;
import org.springframework.web.bind.annotation.ControllerAdvice;
import org.springframework.web.servlet.mvc.method.annotation.RequestBodyAdviceAdapter;
import com.tohours.cnTools.annotation.Decrypt;
import com.tohours.cnTools.utils.AesJsUtils;
import lombok.extern.slf4j.Slf4j;
/**
* @desc 解密含有@Decrypt的参数
* @author RenJie
*/
@Slf4j
@ControllerAdvice
public class DecryptRequestAdvice extends RequestBodyAdviceAdapter {
@Override
public boolean supports(MethodParameter methodParameter, Type targetType,
Class<? extends HttpMessageConverter<?>> converterType) {
// 当某个接口方法或参数上加了@Decrypt注解,才进行解密操作
return methodParameter.hasMethodAnnotation(Decrypt.class)
|| methodParameter.hasParameterAnnotation(Decrypt.class);
}
@Override
public HttpInputMessage beforeBodyRead(final HttpInputMessage inputMessage,
MethodParameter parameter,
Type targetType, Class<? extends HttpMessageConverter<?>> converterType) throws IOException {
InputStream inputStream = inputMessage.getBody();
byte[] bytes = new byte[inputStream.available()];
inputStream.read(bytes);
String requestBody = new String(bytes);
try {
// 结合自己业务针对获取到的requestBody内容进行修改解密等操作
// String decryptData = AesJsUtils.decrypt(requestBody);
String decryptData = requestBody;
//把入参修改为解密后的内容
final ByteArrayInputStream byteArrayInputStream = new ByteArrayInputStream(decryptData.getBytes());
return new HttpInputMessage() {
@Override
public InputStream getBody() throws IOException {
return byteArrayInputStream;
}
@Override
public HttpHeaders getHeaders() {
return inputMessage.getHeaders();
}
};
} catch (Exception e) {
log.error("接口入参解密出错:{}", e.getMessage());
}
return super.beforeBodyRead(inputMessage, parameter, targetType, converterType);
}
}
|
2.3 Controller层
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| package com.tohours.cnTools.controller.test;
import java.util.UUID;
import org.springframework.web.bind.annotation.RequestBody;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController;
import com.alibaba.fastjson.JSONArray;
import com.alibaba.fastjson.JSONObject;
import com.tohours.cnTools.annotation.Decrypt;
import com.tohours.cnTools.annotation.Encrypt;
import com.tohours.cnTools.controller.BaseController;
import com.tohours.cnTools.model.DirectChargeModel;
import com.tohours.cnTools.support.TohoursResponse;
import com.tohours.cnTools.support.TohoursResult;
import com.tohours.cnTools.utils.cq.CQUtils;
import lombok.extern.slf4j.Slf4j;
@RestController
@RequestMapping("/cq")
@SuppressWarnings("rawtypes")
@Slf4j
public class CQTestController extends BaseController {
@RequestMapping(value = "test")
@Decrypt
@Encrypt
public TohoursResult<Object> test(@RequestBody String test) {
log.info("test:" + test);
return TohoursResponse.success(test);
}
}
|
2.4 备注
1
2
3
| 1.接口必须标识了@RequestBody才会被拦截
2.此方法不是很好的拦截所有的请求
3.后面介绍了使用切片方式进行加解密的操作
|
2.5 相关截图
*************感谢您的阅读*************

